Now that virtual meetings have become the norm, ensuring the security and confidentiality of your discussions is paramount.
Cisco Webex is a popular platform for hosting virtual meetings, but like any online service, it's crucial to take advantage of Webex security features and settings to safeguard your meetings.
So, in this comprehensive guide, you'll learn about the ins and outs of Webex security and discover how to protect your Webex meetings in 10 easy steps.
How secure is Cisco Webex?
Webex uses modern End-to-End (E2E) encryption for meetings to ensure meeting confidentiality and secure identities on the Webex application and devices.
It is designed to be secure by default, following the principles of zero-trust security. It offers advanced privacy features and built-in compliance options to meet industry and regional requirements, allowing you to meet and collaborate securely.

It offers a range of certifications and compliance standards:
- ISO 9001, ISO 27001, and ISO 27018 certified
- Service Organization Controls (SOC) 2 Type II, SOC 3 audited
- FedRAMP certified for Webex
- Cloud Computing Compliance Controls Catalogue (C5) attestation
- Privacy Shield Framework certified
However, Webex has had some vulnerabilities that may have led to a compromise in data security. Some recent examples include:
- In 2023, an unauthenticated, remote attacker could conduct a cross-site request forgery (CSRF) attack on an affected system.
- In 2023, multiple vulnerabilities in the web interface of Cisco Webex Meetings could allow an authenticated, remote attacker to conduct a stored cross-site scripting (XSS) attack or upload arbitrary files as recordings.
- In 2022, a remote attacker could conduct a cross-site scripting (XSS) attack or a frame hijacking attack against a user of the web interface.
- In 2021, a vulnerability in the account activation feature could allow an unauthenticated, remote attacker to send an account activation email with an activation link that points to an arbitrary domain.
- In 2021, a vulnerability in the application integration feature of Cisco Webex Software could allow an unauthenticated, remote attacker to authorize an external application to integrate with and access a user's account without that user's express consent.
- In 2021, a vulnerability in the logging mechanisms of Cisco Webex Meetings client software allowed an authenticated, local attacker to gain access to sensitive information.
It has been confirmed that Cisco has released software updates that address these vulnerabilities.
💡 Take Meeting Notes With Confidence
Record and transcribe your meetings, protect your data, and streamline your meeting workflows only with Fireflies.
Key Webex security features & settings
Cisco by Webex prioritizes security with multiple features to safeguard data and protect your online communication.
Let's delve into four key Webex security areas:
1. Identity and device management
The Webex Control Hub is your central interface for managing devices, users, and permissions securely. It supports adaptive authentication, applying a zero-trust approach to security, allowing IT departments to enforce access policies based on risk factors.
Here's what you can manage in the Control Hub:
SAML-Based Single Sign-On
If your organization has its own identity provider (IdP), you can connect it with Control Hub for single sign-on (SSO). This allows your users to use one set of login credentials for both Webex App applications and other tools within your organization.

Idle Timeout
You can set an idle timeout for Webex App web users, which means they'll be automatically signed out of their account after a specified period. This applies to users connected within your organization's network (in-network) and those outside it (off-network).
How to Enable Idle Session Timeout for Off-Network Webex App Web Users:
- Sign in to Control Hub, and under "Management," select "Organization Settings."
- In the "Idle Timeouts" section, turn on "Webex web client idle timeout."
- Under "Off network," choose the idle time duration for off-network Webex App web users.
How to Enable Idle Session Timeout for In-Network Webex App Web Users
- Sign in to Control Hub, and under "Management," select "Organization Settings."
- In the "Idle Timeouts" section, turn on "Webex web client idle timeout."
- Enter a URL that permits CORS requests from web.webex.com.
- Under "In Network," select the idle time duration for in-network Webex App web users.
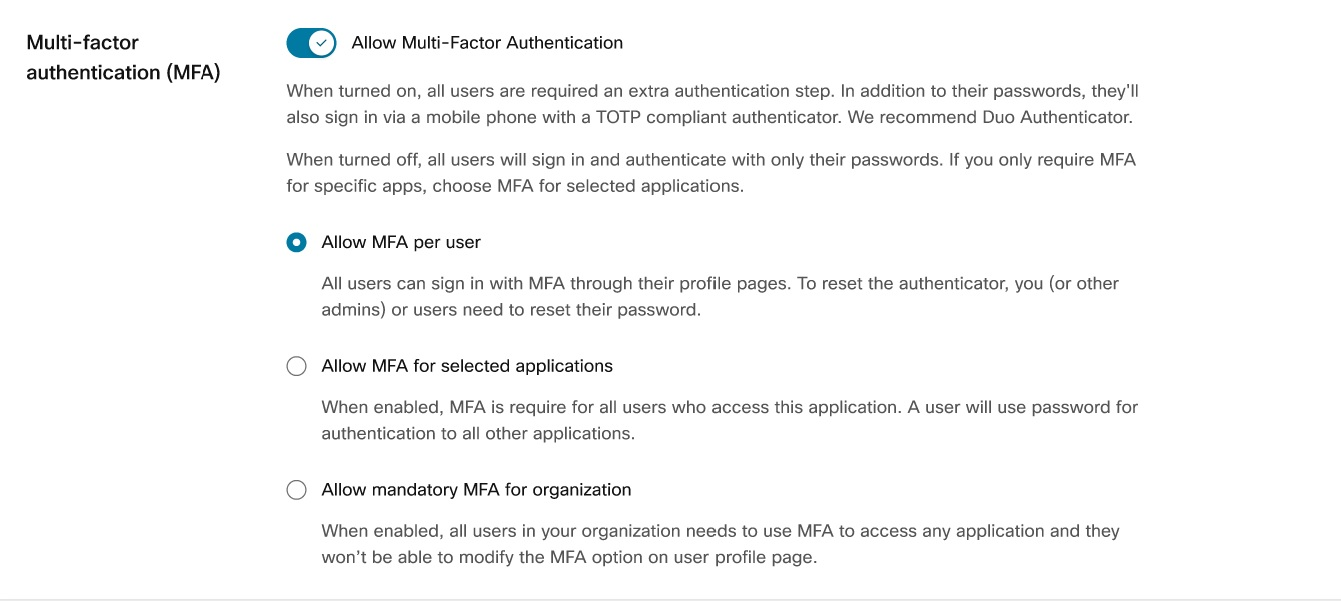
Multi-Factor Authentication (MFA)
Webex allows you to enable Multi-Factor Authentication (MFA) in the Control Hub. This feature adds an extra layer of protection by requiring users to enter codes generated by an authenticator app on their mobile devices when signing in to Webex.
When you activate this setting, affected users must utilize a time-based, one-time password (TOTP) authenticator app.
Popular options include Duo, Windows Authenticator, or Google Authenticator. The authenticator app generates a TOTP token, which users use to verify their identity when accessing Webex.
Here's how to enable MFA in Control Hub:
- Go to the customer view on https://admin.webex.com.
- Navigate to Management > Organization Settings and scroll down to the Authentication section.
- Turn on the switch under Multi-Factor Authentication.
- You can choose from the following settings:
- Allow MFA per user: Activate this option to let individual users enable MFA from their profile page.
- Allow mandatory MFA for selected applications: Enable this setting to make MFA mandatory for users accessing specific applications. You can select the applications that require MFA.
- Allow mandatory MFA for the organization: This option makes MFA mandatory for all users across all applications, and users cannot modify MFA settings from their profile page.
User and group provisioning via SCIM
The integration between directory users and Control Hub uses the System for Cross-domain Identity Management (SCIM) API.SCIM is a recognized open standard that streamlines the automated sharing of user identity details between different identity domains or IT systems.
This standard is specifically tailored to simplify the administration of user identities in cloud-based applications and services. SCIM employs a standardized REST API to achieve this seamless exchange of information.
You can integrate users across various systems using Webex provisioning, including Okta and Azure Active Directory.
Domain claiming
In Control Hub, certain features demand confirmation of your domain ownership. Additionally, domains play a vital role in safeguarding your organization's security and reliability.
Domains also aid in effective user management. You can add, verify, claim, release, or remove domains, especially when they are no longer required.
2. Mobile device management
IT administrators can set specific restrictions and regulations on how users can use Webex on their mobile devices.
They can do this either through Control Hub or by employing services from a third-party provider.
Enterprise Mobility Management (EMM)
EMM empowers your administrators to oversee which devices can access the Webex application and under what conditions.
Here's how it works:
- For devices owned by the enterprise, the devices and their apps are managed through a mobile device management (MDM) app.
- If the devices are personally owned by the users, the Webex app falls under the purview of mobile application management (MAM) apps.
To set up your EMM, Webex recommends the following options (in order of preference):
- Microsoft Intune
- AppConfig
- App Wrapping with IPA and AAB
- Admin controls in Control Hub
Block message copy and file download
Administrators can prevent users from copying and pasting messages within the app or taking screenshots using tools like Microsoft Intune or AppConfig.Admins can also dictate how users share files in your organization's spaces by leveraging Pro Pack within Control Hub.
You can access this feature by:
- Going to https://admin.webex.com
- Then, select Services > Messaging > Collaboration Restrictions.
3. Data Protection
In Webex, data protection is achieved through two main types of data encryption:
- End-to-end encryption for Messages and user-generated Content
- Zero-Trust End-to-End Encryption for Meetings
While both offer enhanced protection against external threats, they differ in terms of the level of confidentiality they provide.
End-to-end encryption relies on the Webex Key Management System (KMS) to manage encryption keys. On the other hand, Zero-Trust Encryption uses Messaging Layer Security (MLS), allowing participants to create a unique encryption key solely accessible to them.
Even the Webex service cannot access this key, hence the name "Zero-Trust."
Enterprise Encryption
Webex offers various levels of data encryption, depending on your subscription plan.
The Enterprise plan offers the highest level of security encryption.
Audit Logs API
Access to administrative changes or actions within the application is often required for compliance purposes.
Full administrators can track alterations to organizational settings and filter actions based on users, date ranges, or specific actions. This information is accessible through the Control Hub and exposed via the REST API for easy access.
Data Loss Prevention (DLP)
Webex takes a dual approach to DLP:
- First, the application keeps users informed about potential data loss risks, external participants, or applied retention policies in the context of their communications. This includes read receipts, space access control, and moderator privileges.
- The second approach allows integration with third-party DLP software to monitor user actions and address potential violations. Businesses can choose out-of-the-box solutions from existing providers, collaborate with Cisco Advanced Solutions to create custom integrations, or build their own solutions using the provided API documentation.
Here are some DLP solutions that seamlessly integrate with the Webex app:
- Broadcom
- Microsoft Cloud App Security (MCAS)
- McAfee (formerly SkyHigh)
- Netskope
- Forcepoint
- Prisma SaaS by Palo Alto Networks
- AGAT
- Theta Lake
- Seqoria

4. Information governance
In this section, you'll see how to manage and govern your information in Webex:
Global Retention Policies
Webex clients have the authority to establish their retention policies, which will be applied universally across all their meeting sites.
Administrators can regulate these retention periods by visiting https://admin.webex.com and navigating to Organizational Settings > Retention.
Webex Meeting Retention Policy
Within this feature, you can specify how long you'd like to retain various types of data, including messages, whiteboards, shared files, meeting recordings, and other content related to meetings.
eDiscovery
For compliance officers and those responsible for ensuring adherence to both internal and external regulations, Webex Control Hub offers a powerful tool: eDiscovery. This tool allows you to search content and metadata posted through the app by specific users.
How to protect your Webex meetings in 10 Steps

When using Webex, you can implement several security measures to protect your meetings. This includes securing your files and messages during transmission and storage, controlling access to your content, and ensuring the safety of your meetings.
Here are some key steps you need to take:
1. Create secure spaces
Webex allows you to create spaces for messaging, meetings, and calls with others, including those from outside your organization.
However, you must consider how to manage access to these spaces effectively. Fortunately, Webex employs advanced cryptography to safeguard the content you share and send.
So, the only people who can view files and messages in a space are those invited to that space or authorized individuals.
2. Add moderators
You can further enhance your Webex security by adding moderators to spaces, especially those containing sensitive information.
Moderators can control space access, add members, oversee shared content, and manage files and messages.
3. Check for external users
Before sending messages, always check for external users in your space to avoid accidentally sharing confidential information.
If there are external users in your meeting, you'll see areas in the spaces highlighted, such as the border, background, the icon in the message area, and their email addresses.
4. Lock your meetings
You can also lock your meetings after they start to prevent unauthorized access. If you don't lock the meeting, anyone with the meeting link can join.
To lock a meeting that you're currently hosting:
- Click the horizontal three-dot icon.
- Click the slider next to Lock Meeting.
5. Remove uninvited participants
To ensure that only authorized attendees are present, you can remove uninvited participants from meetings at any time.

6. Make use of the security features for Site Administrators
Site administrators can enhance security by implementing various measures like:
- Synchronizing employee directories to control access
- Enabling single sign-on (SSO) for easy and secure access
- Enforcing password security standards for additional protection
7. Validate user identity
Another way to ensure the privacy of your meetings is by using roll call to ensure that every attendee's identity is confirmed.
8. Share applications, not screens
When sharing content, it's recommended that you share applications instead of your entire screen to avoid exposing sensitive information accidentally.
9. Exclude meeting passwords from invitations
For highly sensitive meetings, you need to avoid including passwords in email invitations. This prevents unauthorized access when the email is forwarded to unintended recipients.
Once you schedule your meeting, check the Exclude password from email invitation option to ensure the password doesn't appear in the invitation.
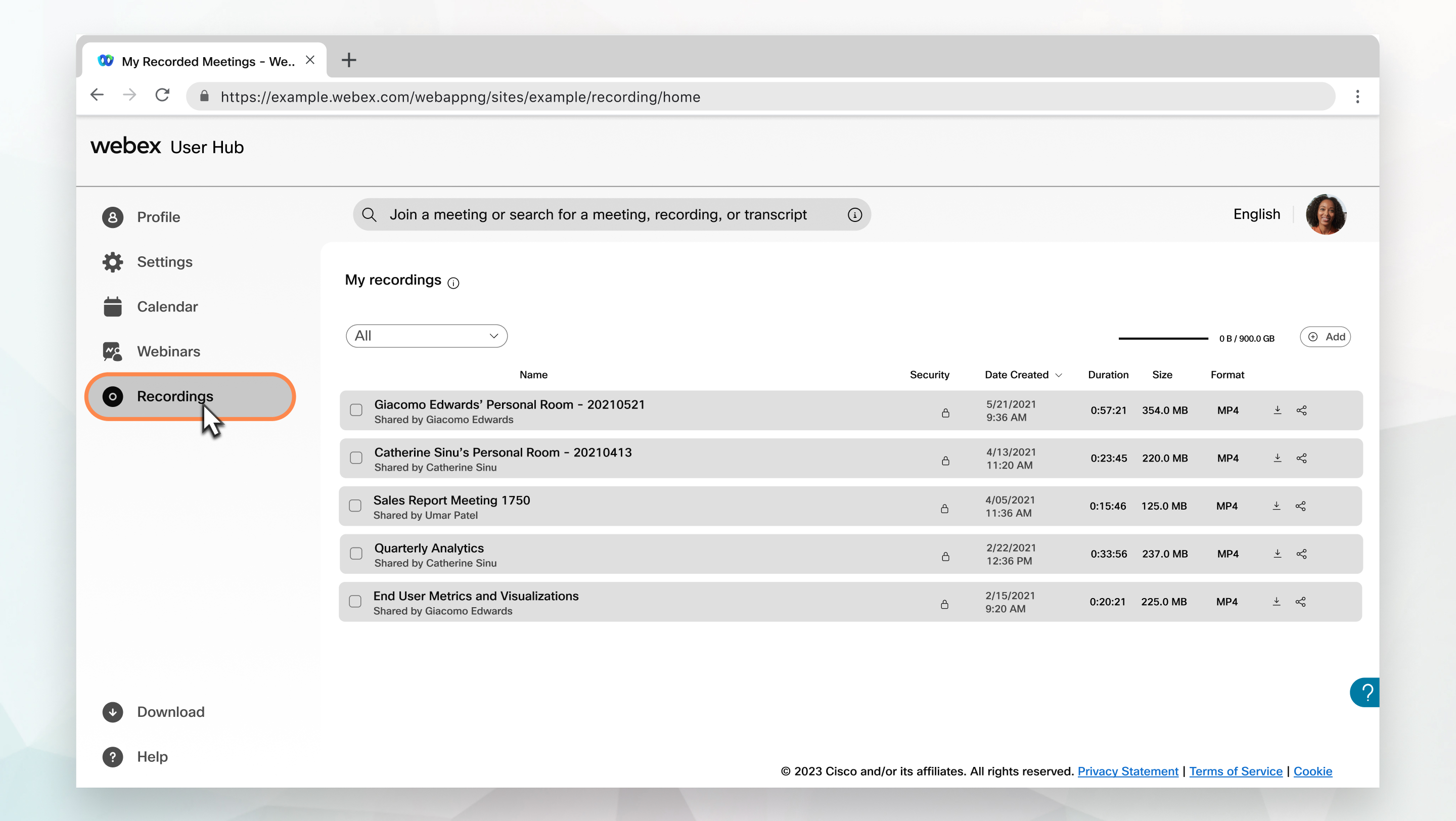
10. Password-protect meeting recordings
It's highly advised that you avoid creating recordings with sensitive information. Add passwords to your recordings to restrict access to authorized individuals if necessary.
To assign passwords to recordings:
- Head on over to your personal Webex user webpage.
- In the Recordings tab, click on the share icon to open the Share Recording Window.
- On the Share Recording Window, click the check box beside Public Link.
- Next, click the check box next to Password protection, then type your desired password in the text field.
- Finally, click Save.

Enhance your Webex meeting security & productivity using Fireflies
Now that you know how to protect your meetings on Webex properly, all that's left to handle is managing your meeting data. And, if you need a tool to help you with that, Fireflies has got you covered!
This intelligent AI meeting assistant seamlessly integrates with Webex to automatically record, transcribe, summarize, and analyze your meetings.
Plus, Fireflies prioritizes your security and privacy when handling your voice and video data, as it complies with the strictest privacy and cybersecurity standards.

Here's how this tool secures your meeting data:
- Security training: All Fireflies employees undergo security training and are trained in best practices for data handling.
- Compliance with SOC 2 Type 2 and GDPR: Fireflies complies with SOC 2 Type 2, HIPAA, and GDPR standards, demonstrating its commitment to maintaining the highest levels of security, privacy, availability, and confidentiality.
- Data encryption: Fireflies uses a robust 256-bit AES encryption for data in storage and a 256-bit SSL/TLS encryption for data in transit.
- AWS hosting: Fireflies' database is hosted in a Virtual Private Cloud with AWS — a provider known for following top IT security standards, including SOC 2 Type II, SOC 3, PCI-DSS certification, and ISO 27001. It also offers private storage, if required.
- Strict data access controls: It enforces strict controls over data access, ensuring that only authorized individuals can access your data.
- Continuous monitoring: Fireflies maintains uptime monitoring and security logging in its production environments, ensuring the availability and security of core services.
- Third-party audits and penetration testing: This tool employs third-party security experts to conduct penetration tests & further secure its IT infrastructure.
- Fireflies has a zero-day data retention policy with vendors who have access to user content (transcription and LLM vendors). None of your data is used for training their AI models.
Overall, you can trust Fireflies to not only accurately capture your meeting data but also safeguard all your conversations!